Defining the security of the objective
Prerequisites
- User with permission for the Objective > Planning menu in SoftExpert Configuration > Configuration > Access group (CM011).
- Previously created objective.
Introduction
SoftExpert OKR provides efficient control over objective access and permissions.
On the objective data screen, users can set it as public or customize the permissions, defining the access as restricted to authorized users.
It is possible to define specific permissions per user, position, team, and organizational unit.
To customize the security of an objective, perform the following steps:
Defining the security of the objective
1. Access the Objective (OK002) menu.
2. Hover the mouse over the desired objective and click on the Open data button that will be displayed.
3. Click on Security, in the upper right corner of the screen that will be displayed.
4. On the screen that will open, click on the  button.
button.
5. By default, the All users option will be selected in the Access type field. Click on this field and select the group type you wish to add to the security. The Specific user, Organizational unit, Position, Department/Position, and Team options are available.
6. At the bottom of the screen, the groups will be listed according to the chosen type. Select the ones you wish to add to the security list.
7. Then, in the Permission profile field, select the permission profile with the controls that will be granted to the selected groups.
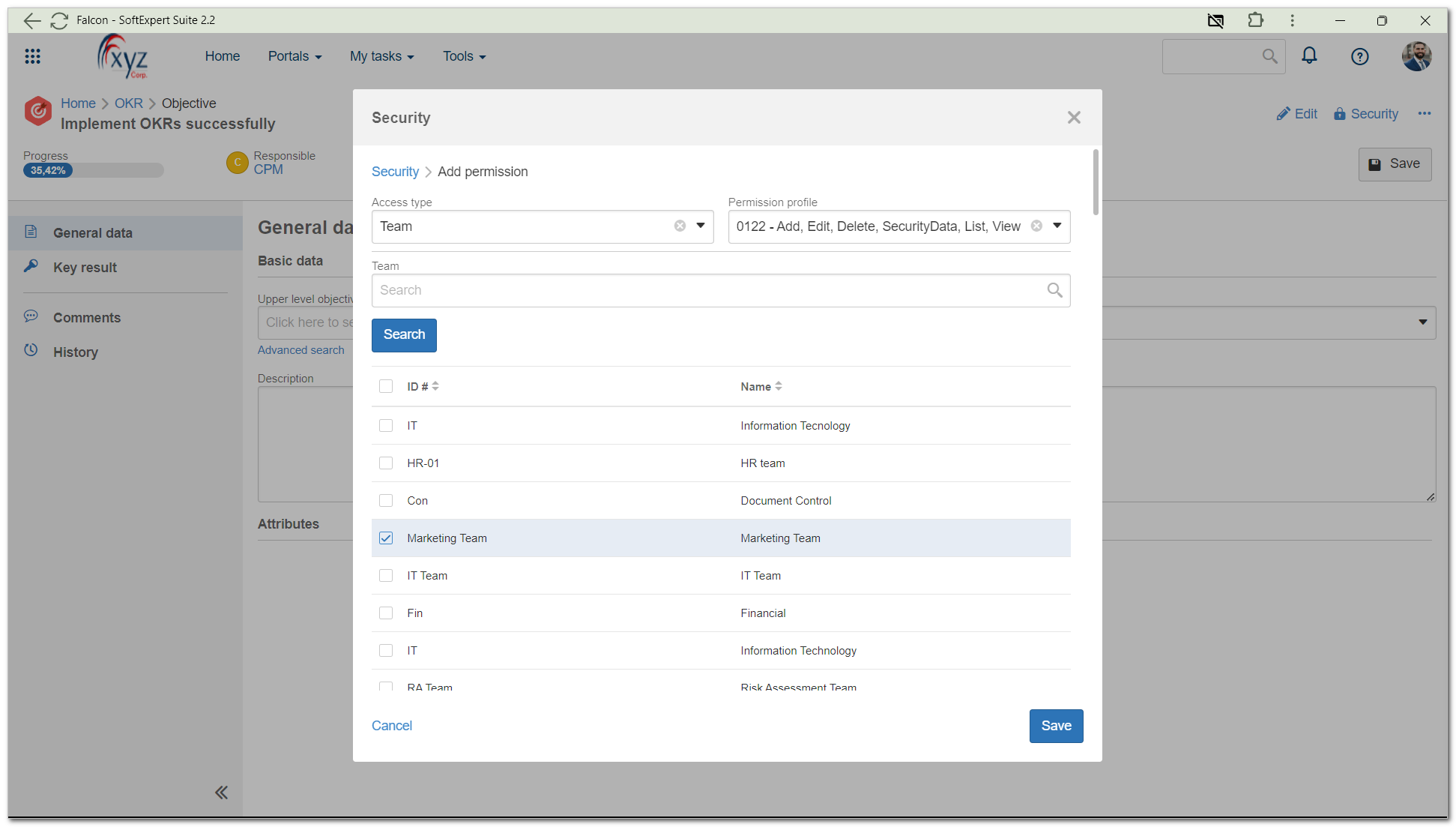
7. Click on Save to apply the security.
8. Repeat the procedure to add all desired groups and their permissions to the security of the objective and its key results.
Key results follow the same security configuration as the objectives to which they are linked.
Remember that adding, editing, and deleting data in the Objective menu requires the appropriate permissions. For further details, click here.
Users who are not on the security list of the objective will not see it listed in the component menus.
Conclusion
Defining the security for the objective enables precise control over access and permissions, adapting to the needs of the organization and ensuring confidentiality.